The Pidgin messaging app removed the ScreenShareOTR plugin from its official third-party plugin list after it was discovered that it was used to install keyloggers, information stealers, and malware commonly used to gain initial access to corporate networks.
The plugin was promoted as a screen-sharing tool for secure Off-The-Record (OTR) protocol and was available for both Windows and Linux versions of Pidgin.
According to ESET, the malicious plugin was configured to infect unsuspecting users with DarkGate malware, a powerful malware threat actors use to breach networks since QBot’s dismantling by the authorities.
Sneaky Pidgin plugin
Pidgin is an open-source, cross-platform instant messaging client that supports multiple networks and messaging protocols.
Although not as popular as in the mid-2000s when multi-protocol clients were in high demand, it remains a popular choice among those seeking to consolidate their messaging accounts into a single app and has a dedicated user base of tech-savvy individuals, open-source enthusiasts, and users who need to connect to legacy IM systems.
Pidgin operates a plugin system that allows users to extend the program’s functionality, enable niche features, and unlock new customization options.
Users can download them from the project’s official third-party plugins list, currently hosting 211 addons.
According to an announcement on the project’s website last week, a malicious plugin named ‘ss-otr’ had slipped into the list on July 6, 2024, and was only pulled on August 16 following a user report about it being a keylogger and screenshot capturing tool.
“A plugin, ss-otr, was added to the third party plugins list on July 6th. On August 16th we received a report from 0xFFFC0000 that the plugin contained a key logger and shared screen shots with unwanted parties.
We quietly pulled the plugin from the list immediately and started investigating. On August 22nd Johnny Xmas was able to confirm that a keylogger was present.” – Pidgin
A red flag is that ss-otr only provided binaries for download and not any source code, but due to the lack of robust reviewing mechanisms in Pidgin’s third-party plugin repository, nobody questioned its security.
Plugin leads to DarkGate malware
ESET reports the plugin installer is signed with a valid digital certificate issued to INTERREX – SP. Z O.O., a legitimate Polish company.
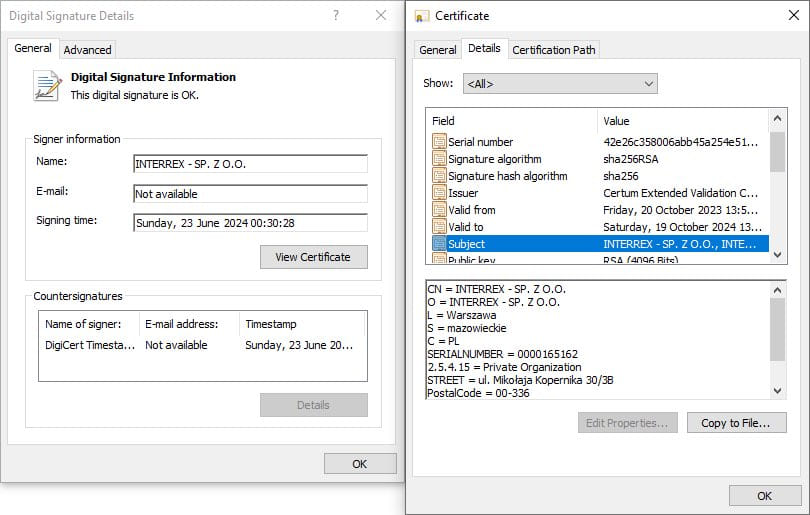
Source: ESET
The plugin offers the advertised functionality of screen sharing but also contains malicious code, allowing it to download additional binaries from the attacker’s server at jabberplugins[.]net.
The downloaded payloads are either PowerShell scripts or the DarkGate malware, which is also signed by an Interrex certificate.
A similar mechanism is implemented for the Linux version of the Pidgin client, so both platforms are covered.
ESET says that the same malicious server, which has been taken down now, hosted additional plugins named OMEMO, Pidgin Paranoia, Master Password, Window Merge, and HTTP File Upload.
These plugins were almost certainly also delivering DarkGate, indicating that ScreenShareOTR was just one small part of a broader-scale campaign.
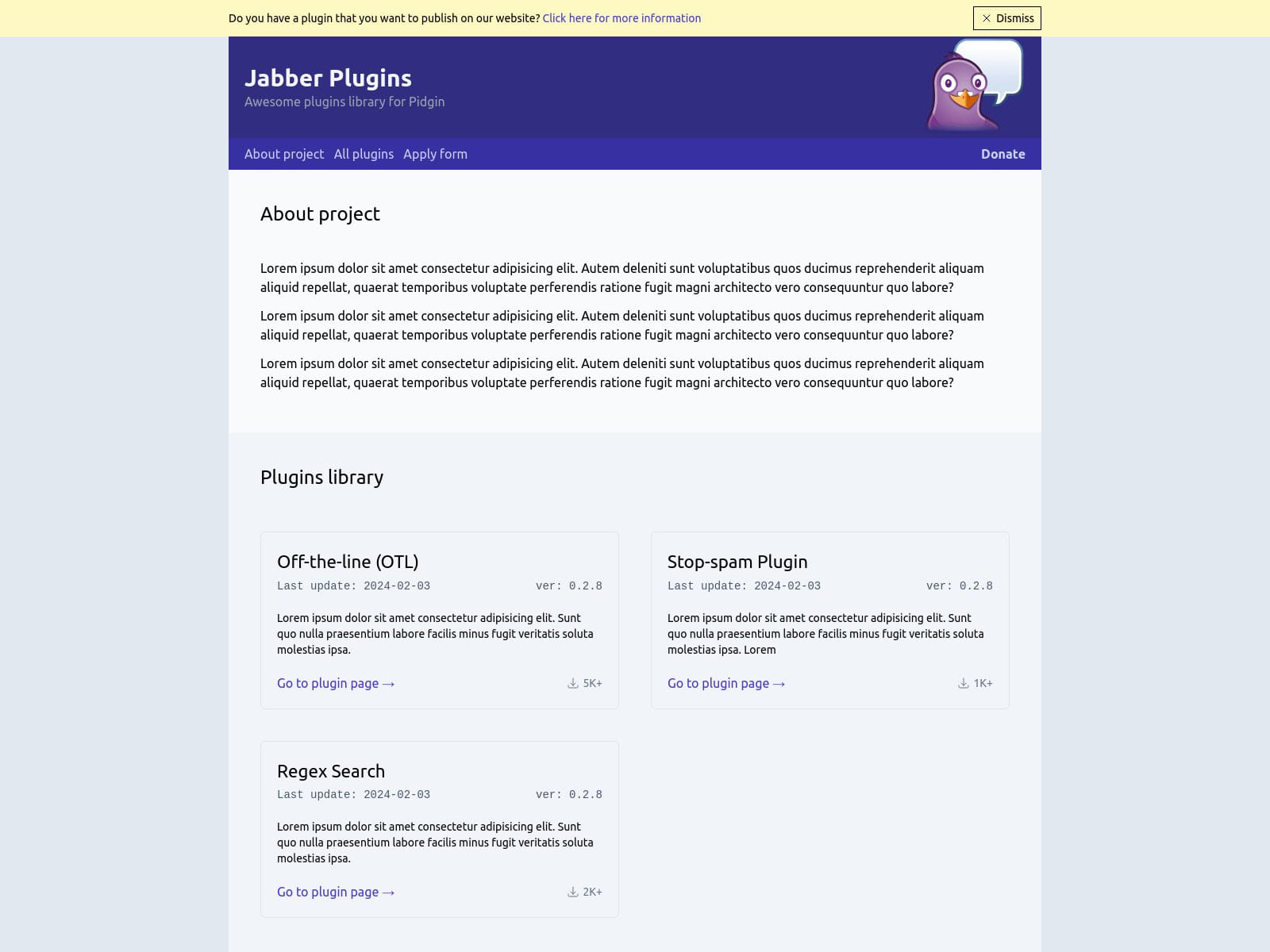
Source: ESET
Those who installed it are recommended to remove it immediately and perform a full system scan with an antivirus tool, as DarkGate may be lurking on their system.
After publishing our story, Pidgin’s maintainer and lead developer, Gary Kramlich,
gr****@ma******.social
/113035335884182662″ target=”_blank” rel=”nofollow noopener”>notified us on Mastodon to say that they do not keep track of how many times a plugin is installed.
To prevent similar incidents from happening in the future, Pidgin announced that, from now on, it will only accept third-party plugins that have an OSI Approved Open Source License, allowing scrutiny into their code and internal functionality.
Update 8/27/24: Updated story to note that Pidgin does not keep track of plugin downloads.